Background
Recently I was engaged to assist a customer with an interesting issue. This customer follows the guideline at https://docs.microsoft.com/en-us/previous-versions/azure/ad/graph/howto/azure-ad-graph-api-directory-schema-extensions to create a custom User attribute as a Directory schema extension and then assigns a value to the attribute. As an example, I have a few custom attributes created this way as can be seen by Microsoft Graph Explorer:
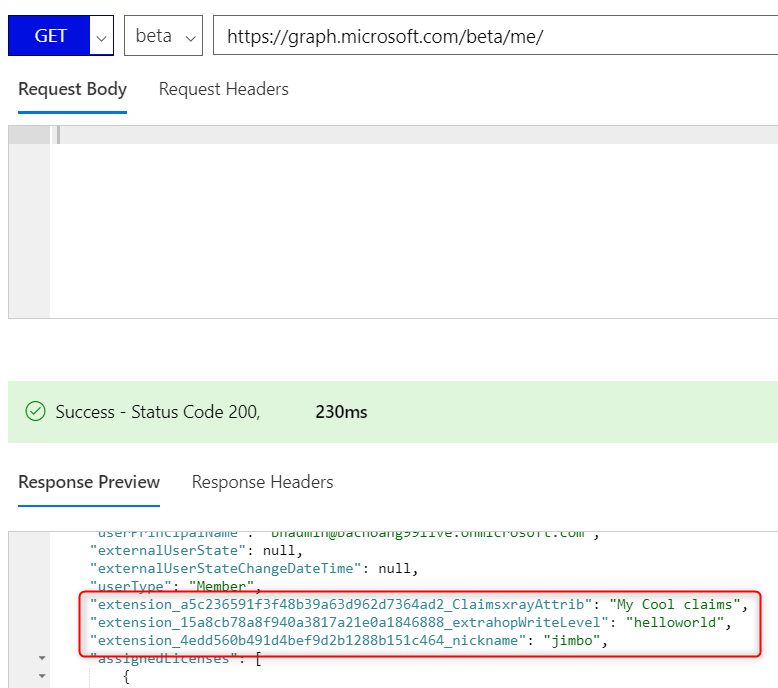
The customer wants to have this custom attribute returned as a claim in a SAML token when using an Enterprise Application to sign users in.
Note: By default, Azure AD only returns the claim if its value is not null.
Resolution
After spending some time researching, the only way to achieve this is by using claims mapping policy as detailed below. It’s important to note that custom attributes created this way do not show up in the Enterprise Application’s Single Sign-on User Attributes & claims customization wizard.
-
Run the following Azure AD Powershell (must use AzureAD-Preview module) command to log in with an organizational admin account
Connect-AzureAD
-
Create a new claims mapping policy similar to the following. In this example, I want to include the customer attribute ‘extension_a5c236591f3f48b39a63d962d7364ad2_ClaimsxrayAttrib’ in my SAML token:
New-AzureADPolicy -Definition @(‘{“ClaimsMappingPolicy”:{“Version”:1,”IncludeBasicClaimSet”:”true”, “ClaimsSchema”: [{“Source”:”user”,”ExtensionID”:”extension_a5c236591f3f48b39a63d962d7364ad2_ClaimsxrayAttrib”,”SamlClaimType”:”http://schemas.xmlsoap.org/ws/2005/05/identity/claims/extension_a5c236591f3f48b39a63d962d7364ad2_ClaimsxrayAttrib”}]}}’) -DisplayName “ClaimsxrayPolicy3” -Type “ClaimsMappingPolicy“
-
Assign the policy to the Enterprise Application:
Add-AzureADServicePrincipalPolicy -Id <Enterprise App objectID> -RefObjectId <Policy ID>
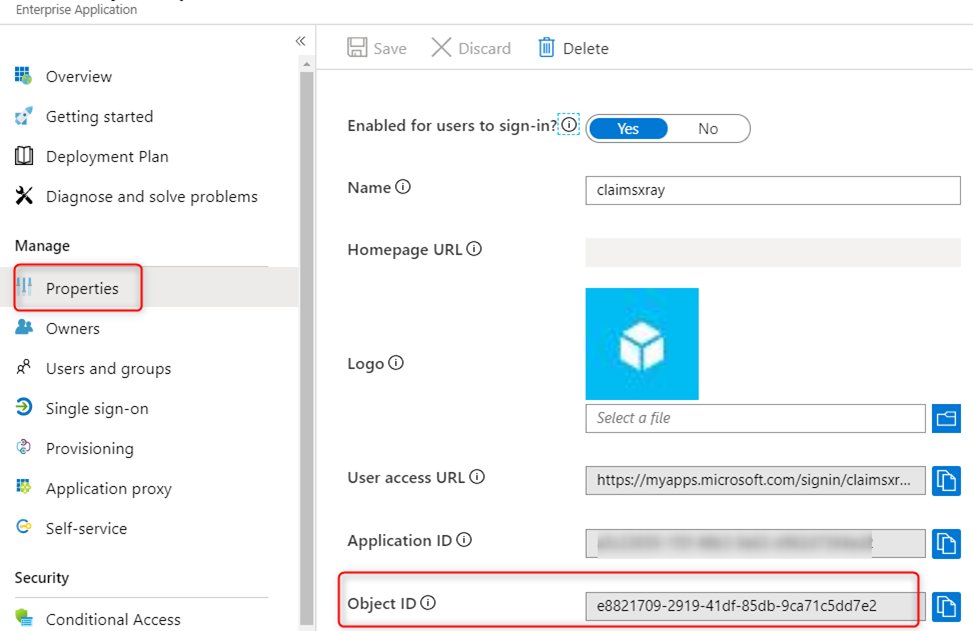
To find the Enterprise App Object ID, look at the Object ID field from the ‘Properties’ blade for the Enterprise Application:
If configured properly you should see desired claim in the AttributeStatement section of the SAML token:
<AttributeStatement>
…
<Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/extension_a5c236591f3f48b39a63d962d7364ad2_ClaimsxrayAttrib">
<AttributeValue>My Cool claims</AttributeValue>
</Attribute>
</AttributeStatement>